As remote work continues to rise, the security of corporate IT infrastructure has become more vulnerable than ever. A 2022 study by Stellar Cyber found that 72% of security teams experienced burnout due to the overwhelming number of cyberattacks they had to deal with.
While traditional security tools such as firewalls, antivirus software, and Intrusion Detection Systems (IDS) are still widely used to protect systems and data, they often fall short when it comes to detecting, preventing, and responding to today’s increasingly sophisticated and complex threats.
That’s why businesses need a more integrated and adaptive security approach, one that can connect the dots between different layers of defense and respond quickly when threats arise. This is where XDR (Extended Detection and Response) comes in.
So, what is XDR exactly, and why is it considered more effective in preventing and responding to cyberattacks compared to traditional solutions like antivirus or firewall systems? Let’s dive deeper.
What is XDR?
XDR (Extended Detection and Response) is an advanced cybersecurity approach that integrates multiple security solutions to detect, investigate, and respond to cyber threats across different platforms.
Unlike traditional security tools that operate in silos, XDR expands the scope of threat detection and incident response by unifying data from various sources, including endpoints, networks, cloud environments, and applications. This enables organizations to gain a more comprehensive and real-time view of potential threats.
The main idea behind XDR is to provide a smarter, automated, and unified defense system. By consolidating visibility and response capabilities, XDR helps businesses better understand evolving threats and strengthen their ability to handle increasingly complex cyberattacks.
Why XDR is Essential for Business Continuity Today
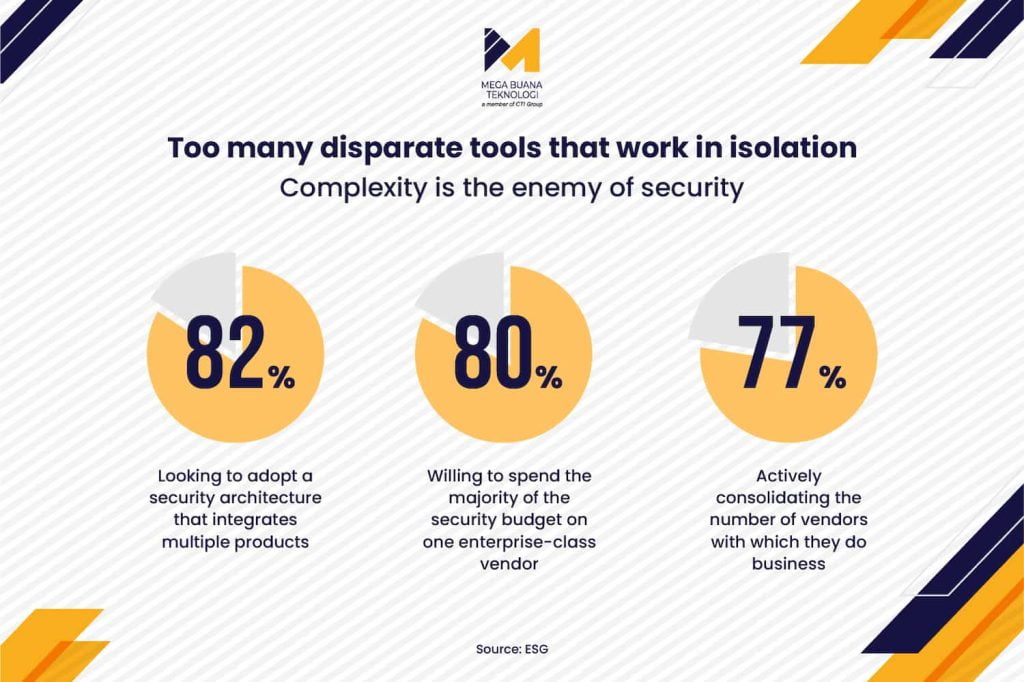
In today’s increasingly complex cybersecurity landscape, XDR (Extended Detection and Response) has become more crucial than ever. Businesses are now relying on a growing mix of cloud services, applications, and connected devices, each introducing new potential points of vulnerability.
The rapid expansion of services like Software-as-a-Service (SaaS) and Infrastructure-as-a-Service (IaaS) also adds pressure on security teams, who must continuously monitor and protect every connected element within the organization.

Without comprehensive protection, security gaps across endpoints, emails, networks, and applications can be easily exploited, potentially disrupting business operations.
XDR addresses this challenge by offering an integrated, end-to-end approach to detecting, preventing, and responding to threats, helping organizations maintain business continuity even amid the ever-evolving cyber risk landscape.
Key Capabilities of XDR
XDR (Extended Detection and Response) membantu mengoordinasikan deteksi dan respons ancaman siber dalam satu platform, memudahkan perusahaan menghadapi serangan yang semakin kompleks. Selain itu, berikut lima kemampuan utama XDR:
Automated Incident Investigation
XDR automatically correlates small alerts and turns them into a complete picture of the threat. This allows analysts to understand and respond faster, without the need to manually piece together scattered data.
Automated Attack Containment
Using real-time detection, XDR can isolate infected devices or user accounts, stopping the attack before it spreads further across the network.
Full Attack Chain Visibility
XDR offers end-to-end visibility into attack paths that traditional tools often miss, helping security teams accelerate investigation and mitigation efforts.
Automated Recovery
XDR can automatically restore compromised assets, such as stopping malicious processes or removing suspicious email rules, allowing teams to focus on higher-priority threats.
AI and Machine Learning Integration
By leveraging AI and Machine Learning, XDR continuously monitors suspicious behavior and responds to threats in real time, delivering faster and more efficient cyber defense.
Core Security Components of XDR
The main components of XDR (Extended Detection and Response) include.
- Endpoint Detection and Response (EDR): Detects and responds to threats targeting endpoint devices.
- Network Detection and Response (NDR): Monitors and protects network traffic against suspicious activities.
- Email Security: Shields users from phishing attacks and email-borne malware.
- Cloud Security: Secures data, workloads, and applications across cloud environments.
- Threat Intelligence: Provides up-to-date insights into evolving cyber threats.
- Security Information and Event Management (SIEM): Collects and analyzes log data from multiple sources to identify anomalies.
- Identity and Access Management (IAM): Manages user identities and controls access to critical systems.
- Security Orchestration, Automation, and Response (SOAR): Automates workflows and coordinates response actions to threats.
- Application Security: Protects applications from vulnerabilities and exploit attempts.
- User and Entity Behavior Analytics (UEBA): Analyzes user behavior patterns to detect unusual or risky activities.
XDR integrates all these components into a single, cohesive framework, enabling a more holistic, efficient, and proactive cybersecurity strategy.
Why Open XDR is the Smartest Choice for Modern Cybersecurity
According to Gartner, there are three types of XDR approaches: Closed, Anchored, and Open XDR. Among these, Open XDR stands out as the most flexible and future-ready option for organizations that want maximum efficiency and adaptability in their security operations.
Here’s why Open XDR is the better choice.
Flexible Integration Freedom
Open XDR gives you the freedom to integrate best-of-breed security tools from different vendors, without being locked into a single ecosystem that may have limitations.
This flexibility is especially valuable for organizations that have already invested in specific security technologies or want to leverage the strongest solutions in every category, from endpoint and network to cloud and application security.
More Holistic and Efficient Protection
With Open XDR, you can consolidate data from multiple sources, including endpoints, networks, clouds, and applications, to gain deeper and broader visibility into potential threats.
This not only accelerates detection and response but also eliminates data silos that often hide undetected attacks. The result is a more unified and responsive security posture.
Freedom from Vendor Lock-In
Closed XDR solutions often tie organizations to a single vendor’s ecosystem, which might not always align with every operational need.
Open XDR, on the other hand, allows you to choose and combine technologies that best fit your organization’s specific requirements, giving you true freedom to build the most effective cybersecurity stack without compromise.
Stellar Cyber: The Best Open XDR Choice for Your Organization
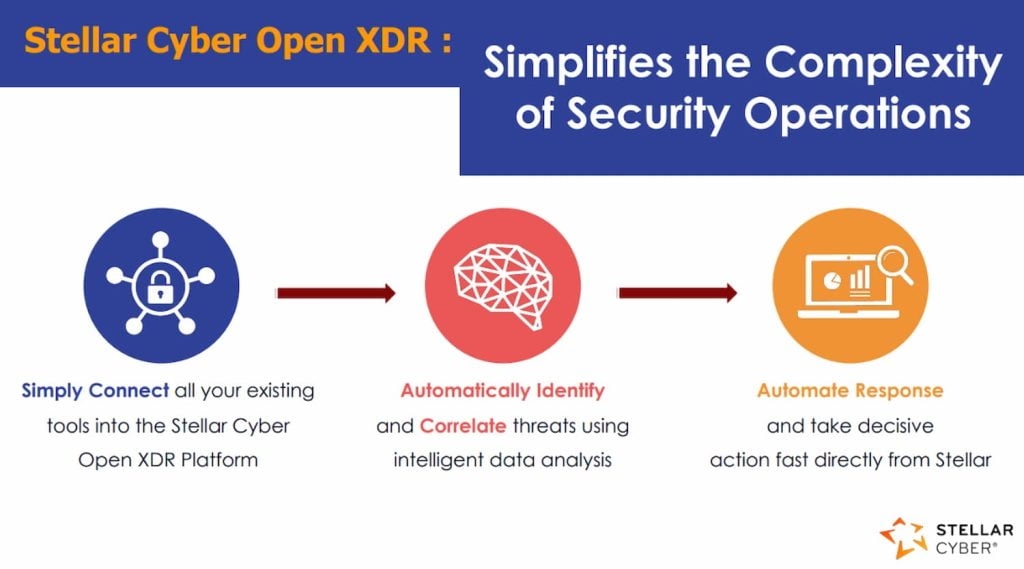
As a recognized leader in the Open XDR market, Stellar Cyber delivers a security solution that is integrated, comprehensive, and highly flexible, ideal for organizations looking to protect their IT infrastructure more smartly and efficiently. Here’s why Stellar Cyber stands out as a top Open XDR platform.
Seamless Integration
Easily connect all your existing security tools to the Stellar Cyber Open XDR platform. This ensures that every part of your security ecosystem works together in one unified system.
Accurate and Automated Threat Detection
Stellar Cyber intelligently identifies and correlates threats using advanced data analytics, giving you a clear and real-time view of potential cyber risks.
Automated Response Actions
Respond to threats automatically and take immediate, precise action directly from the platform. This minimizes risk and reduces potential damage before it escalates.
With Stellar Cyber, your organization gains a powerful, unified, and easy-to-operate cybersecurity solution, making it the best-in-class choice for modern Open XDR implementation.
Get Stellar Cyber’s XDR Solution Exclusively from MBT
As an authorized distributor of Stellar Cyber, Mega Buana Teknologi (MBT) provides expert IT specialists who help you avoid the trial-and-error phase when deploying Stellar Cyber’s XDR solution.
With 24/7 IT support, MBT ensures a seamless experience, from initial assessment to post-deployment maintenance, giving your organization complete confidence in its cybersecurity posture.
Contact us today to learn more about Stellar Cyber’s powerful XDR capabilities and discover how you can start strengthening your cyber defense now.
Author: Ary Adianto
Content Writer CTI Group




